Hi all, long time no see.
I’m back on iOS security testing, which is my best hobby.
Let’s start!
- What is iOS? iOS is a mobile operating system that powers Apple mobile devices, including the iPhone, iPad, and iPod Touch
- Let’s dig into iOS Security Architecture:
- Hardware Security
- Secure Boot
- Code Signing
- Apple has implemented an elaborate DRM system to make sure that only Apple-approved code runs on their devices, that is, code signed by Apple.
- Sandbox: The appsandbox is an iOS access control technology. It is enforced at the kernel level. Its purpose is limiting system and user data damage that may occur when an app is compromised.
- The app process is restricted to its own directory (under /var/mobile/Containers/ Bundle/Application/ or /var/containers/Bundle/Application/, depending on the iOS version) via a chroot-like process.
- The
mmapandmmprotectsystem calls are modified to prevent apps from making writable memory pages executable and stopping processes from executing dynamically generated code. In combination with code signing and FairPlay, this strictly limits what code can run under specific circumstances (e.g., all code in apps distributed via the App Store is approved by Apple). - Processes are isolated from each other, even if they are owned by the same UID at the operating system level.
- Hardware drivers can’t be accessed directly. Instead, they must be accessed through Apple’s public frameworks.
- Encryption and Data Protection
- General Exploit Mitigations
For more details here: https://mas.owasp.org/MASTG/iOS/0x06a-Platform-Overview/#ipa-payloads-a-closer-look
4. Next about what is jailbreaking/jaibroken?
Jailbreaking is a term used to describe the process that allows you to truly unlock the potential of your iOS device. Apple’s mobile operating system is known for its security and that’s partly because of how locked-down it is. Jailbreaking your device will allow you to break those restrictions and customize your device to how you like it.
Jailbreaking gives you the ability to install custom applications and “tweaks” (modifications) from a package manager to customize and enhance the user experience. Jailbreaking is free and easy on most devices.
5. Types of Jailbreak
There are 4 main types of jailbreaks:
- Untethered Jailbreak: Permanent Jailbreak, the device will be jailbroken even after a reboot.
- Tethered Jailbreak: Temporary Jailbreak, after a reboot device, will be back to its normal state.
- Semi-tethered Jailbreak: A semi-tethered jailbreak is one where the device can start up on its own, but it will no longer have a patched kernel, and therefore will not be able to run modified code.
- Semi-untethered Jailbreak: A semi-untethered jailbreak is similar to an untethered jailbreak in that it allows the device to boot up on its own. The device startup sequence is unaltered on each boot, and it boots into its original, non-jailbroken state. However, rather than using a computer to jailbreak, as in a tethered or semi-tethered case, the user can re-jailbreak their device using an app that runs on their device.
Details here: https://ios.cfw.guide/types-of-jailbreak/
6. IPA structure?
- App binary: The executable file containing the compiled (unreadable) application source code.
- Info.plist: Configuration information, such as bundle ID, version number, and application display name.
- Frameworks: List of dynamic libraries.
- Embedded.mobileprovsion: These are certificates.
Now, we have knowledge about iOS security testing.
Let’s start to lab for hand-on DIVA v2, you can download here:
https://github.com/prateek147/DVIA-v2
Now, download it.
Preparation: iPhone 7,… with iOS 15 (Palera1n rootless)
Install Frida in Sileo with repo: build.frida.re
Go to Sileo -> install TrollStore Helper -> install Trollstore.
Now, install IPA with Trollstore.
Other devices iOS <15, you can install AppSync for install iPA via Filza.
Let’s first challenge:
Local Data Storage.
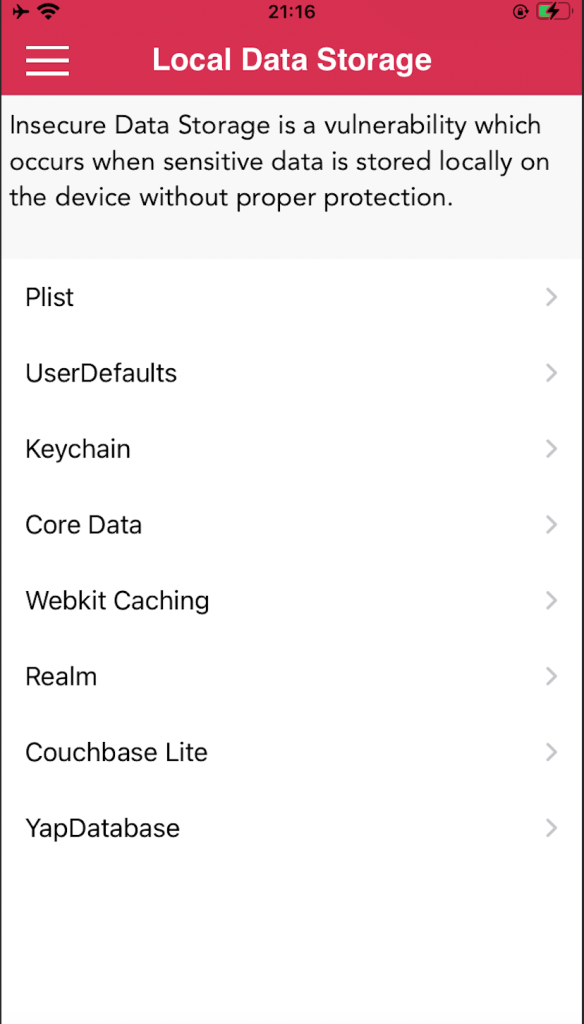
This is the first challenge
In plist, now we can access this phone via SSH.
Go to Sileo -> search openssh and install it.
Now we can ssh into the device.

As we know that: App sandbox user data in:
/var/mobile/Containers/Data/Application/<app-id>/Documents
You can find app-id via many ways. The simple way is via Filza as:
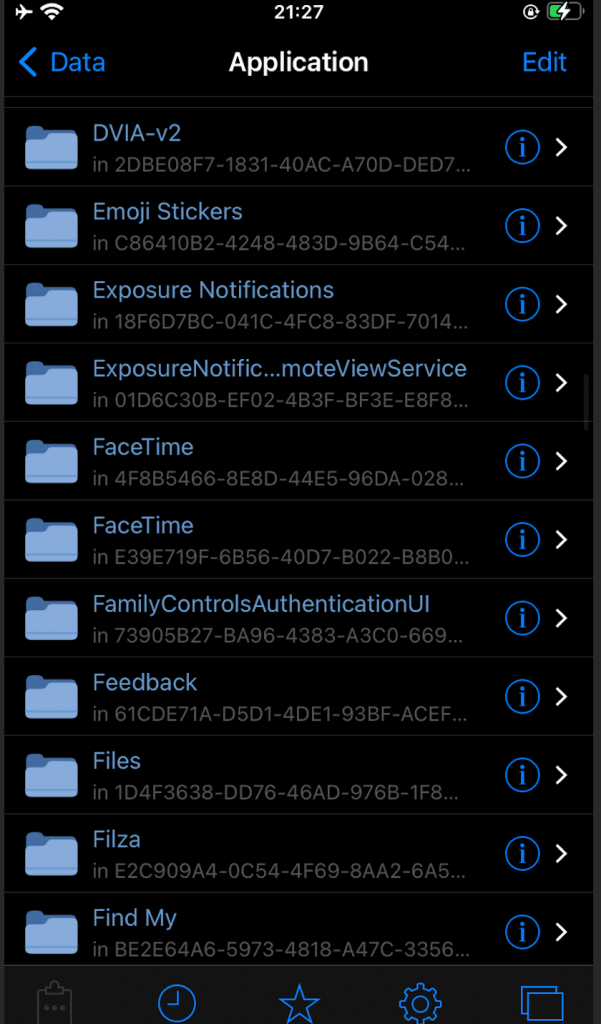
It is here:

Now, go to UserDefaults:
3 ways to read data in UserDefault:
Way 1: Use objection.
objection -g com.highaltitudehacks.DVIAswiftv2 explore
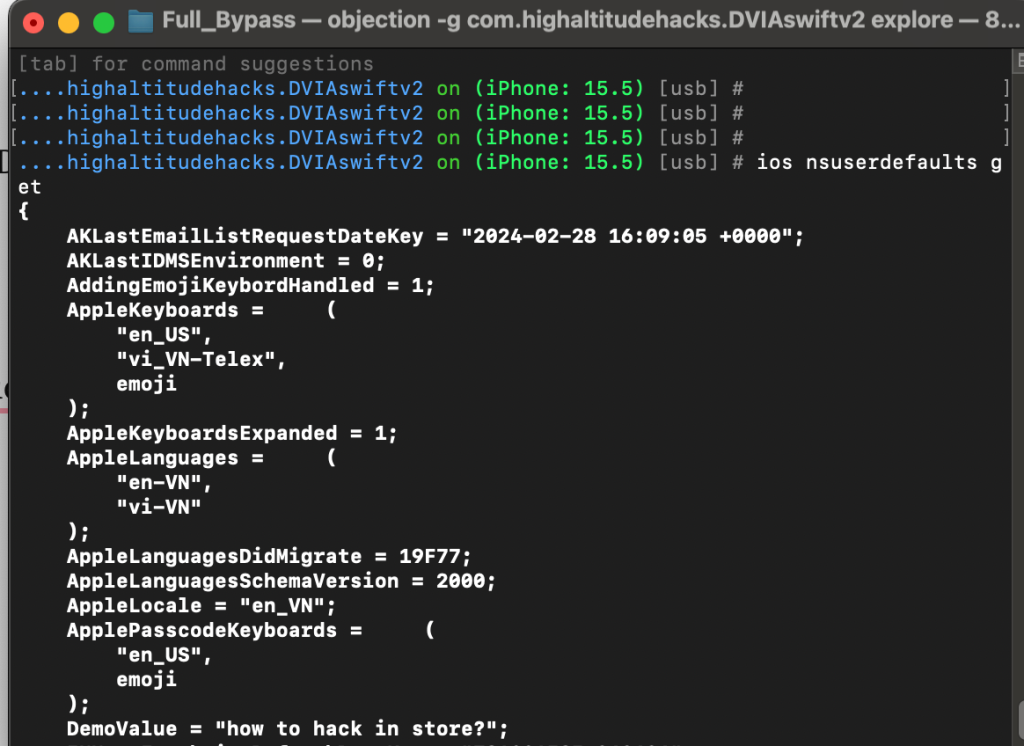
Way 2: Use ssh.
/var/mobile/Containers/Data/Application/<app-id>/Library/Preferences

Way 3: Write Frida script to get data as:
Next to keychain.
We can use objection to dump keychain as:

Next to Core data:
Core Data: Persist or cache data on a single device, or sync data to multiple devices with CloudKit.
Some ways, you can try in other blogs.
/var/mobile/Containers/Data/Application/<app-id>/Library/Application Support
Goto Sileo -> install sqlite3.
Now you can read as:
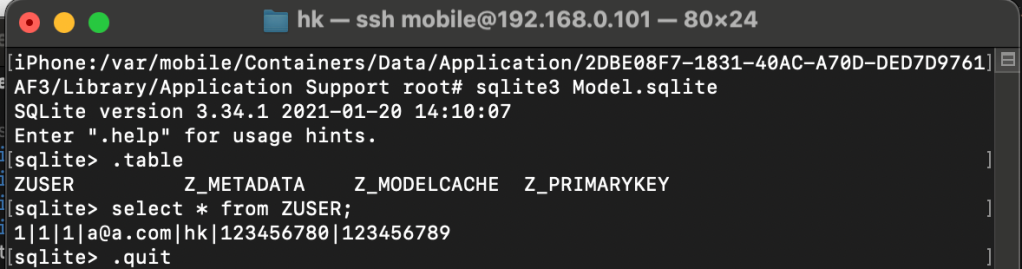
The same way to Couchbase Lite:
/var/mobile/Containers/Data/Application/<app-id>/Library/Application Support/CouchbaseLite
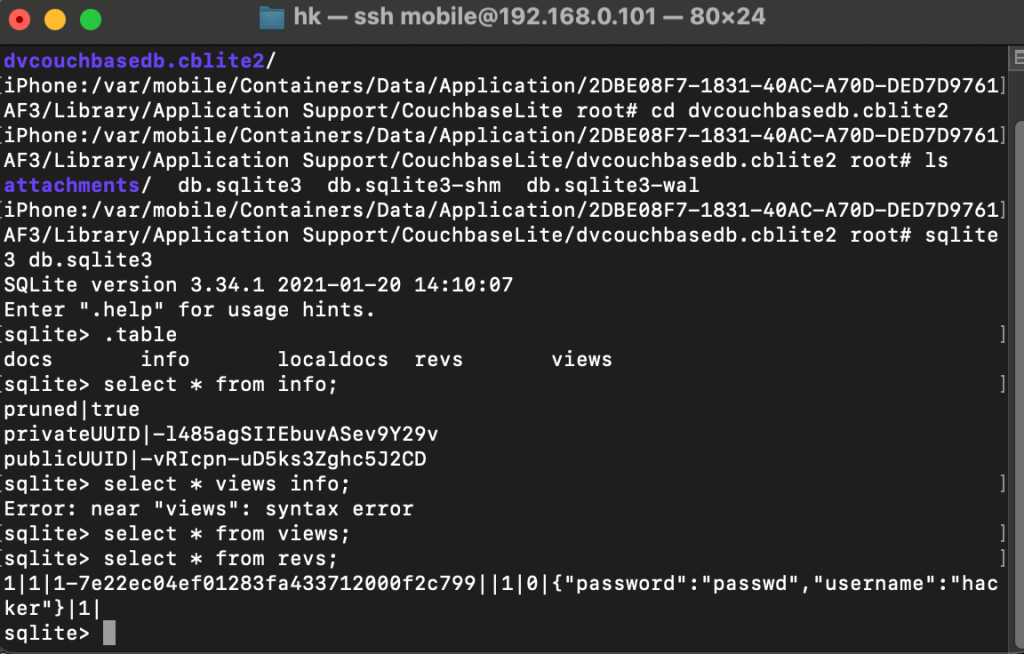
The same to YapDatabase:
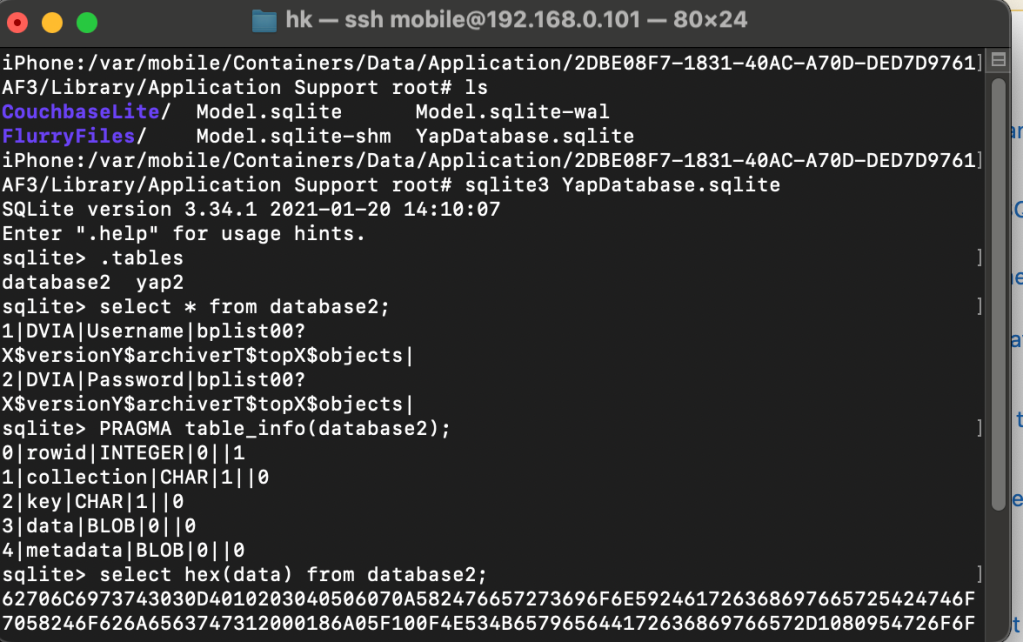
Now, convert hexa to string to get data as:


Next to Webkit caching:
/var/mobile/Containers/Data/Application/<app-id>/Library/Caches/WebKit/NetworkCache/Version
And cat all file to find sensitive data.
Next to Realm.
/var/mobile/Containers/Data/Application/<app-id>/Documents

How to read/open default.realm?
Download and open with https://github.com/realm/realm-studio.
Thanks for reading part 1.